Akamai EdgeWorkers
Akamai integration for Bot Protection
Before the Akamai EdgeWorker processes a client request, the proxy will call the DataDome API through the HttpRequest module. Depending on the API response, the integration will either block the request and return the content provided by DataDome, or let Akamai proceed with the regular process. The module has been developed to protect the users’ experience: if any errors were to occur during the DataDome process or if the call to DataDome reaches a timeout, the integration will automatically assume a 200 for that request, and continue the process normally.
Prerequisites
This article assumes that you already have:
- Access to the Akamai Dashboard: https://control.akamai.com/apps/home-page/
- Set up the concerned website as an Akamai Property: https://control.akamai.com/apps/property-manager
- Enabled access to the Akamai EdgeWorkers from the Akamai Marketplace: https://control.akamai.com/apps/marketplace-ui
- Ability to create EdgeWorkers: https://control.akamai.com/apps/edgeworkers/
- If you are using Akamai SiteShield, ensure that your SiteShield map setup allows traffic worldwide, as DataDome is deployed globally. This means allowing the largest possible Akamai IP range to connect to your origin. You can work with Akamai to review and validate the appropriate IP ranges for your setup.
- If you are using Phased release cloudlet make sure the path
/validate-requestdoes not match it
Installation
Setting up the EdgeWorker
- Access the EdgeWorkers Management screen at: https://control.akamai.com/apps/edgeworkers.
- Click on the Create EdgeWorker ID button at the top-right.
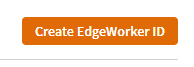
- The Create EdgeWorker ID modal is shown
- Set the name of the EdgeWorker to EW_DataDome_Protection
- The Group refers to which set of access permissions you are going to apply to the newly created EdgeWorker
- Set the Resource Tier to Basic Compute
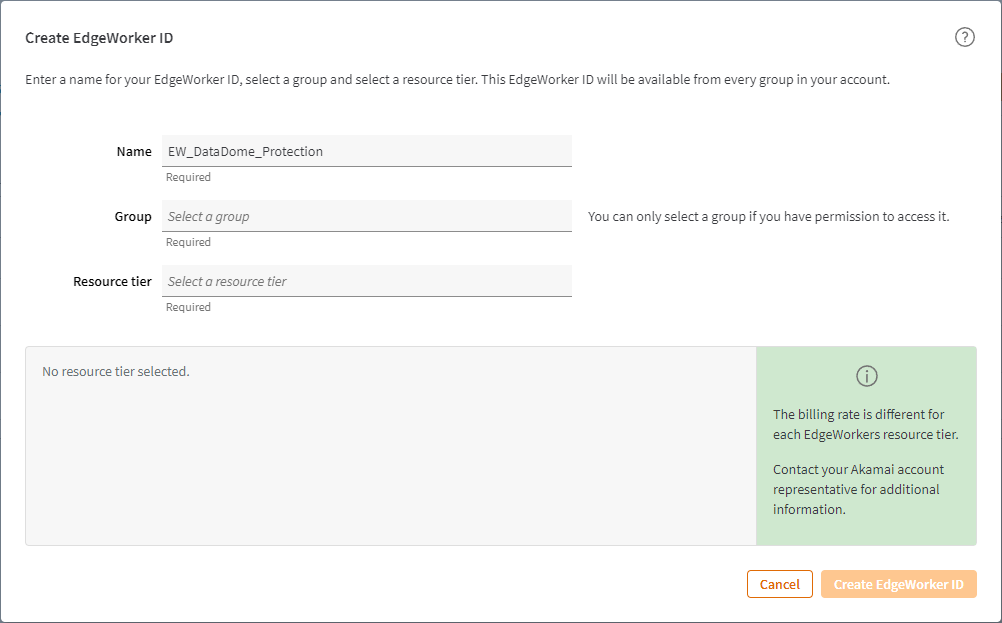
- A new row will be added to the EdgeWorker table.
By default the EdgeWorker is not enabled in either Staging or Production
- Click on the respective ID, the EdgeWorker ID details page will be shown.
- Click on the Create Version button, the Create Version modal will be shown.
- Drag and drop the provided tar file in the droppable area.
- The droppable area should validate the dropped bundle
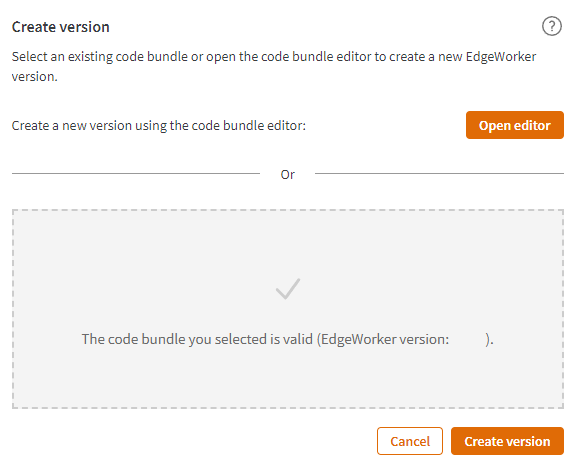
- Click on the Create version button on the bottom-right of the modal.
- A row will be added to the Versions table.
- Click on the last version added, the EdgeWorker version details page will be shown.
- Click on the Activate version button, the Activate version modal will be shown.
- Choose a Network to deploy this version to.
It is recommended that deployments are first done in Staging to be validated, then deployed to Production when all the necessary checks are made
EdgeWorker environments are updated separately, the activation process needs to be done twice to update both the Staging and the Production environments
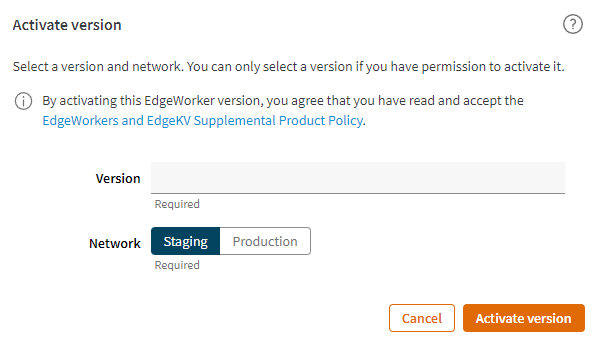
- Click on the Activate version button to proceed; the EdgeWorker version details page will get updated with a notification on the top-right and a progress bar.
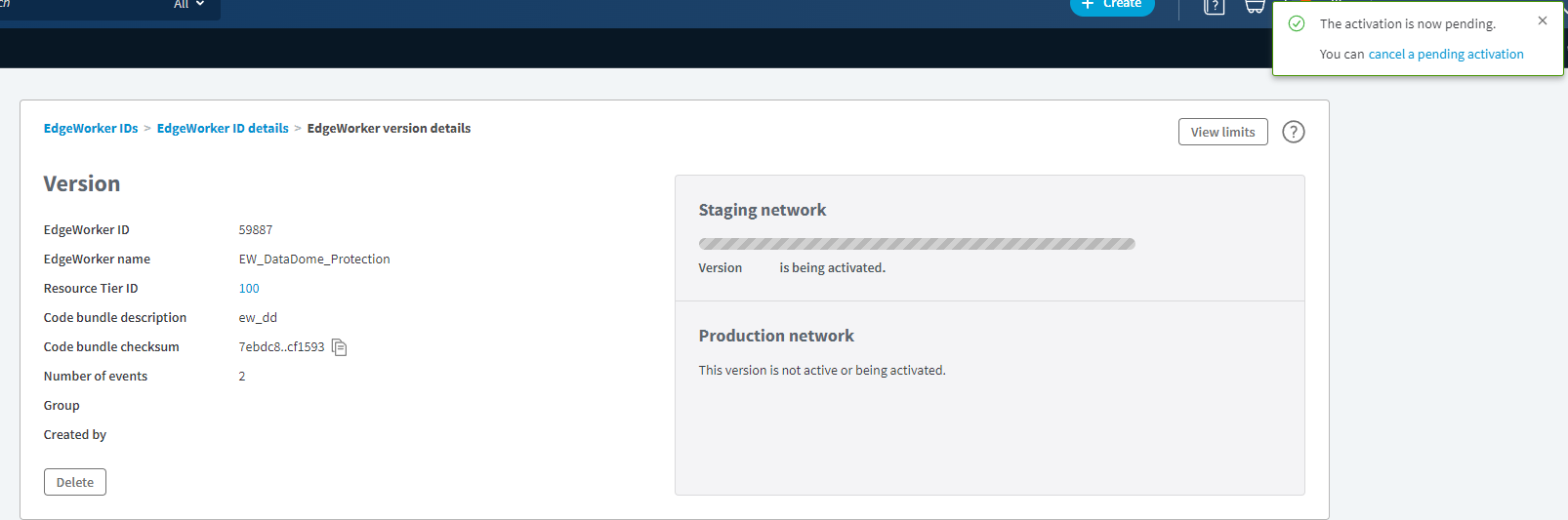
- Kindly wait until the progress bar is full and green, and the version is marked as active in that environment.
Changes in the Property Manager
Step 0: Create a new version of your Akamai property
- Go to your Akamai property you would like to protect with DataDome.
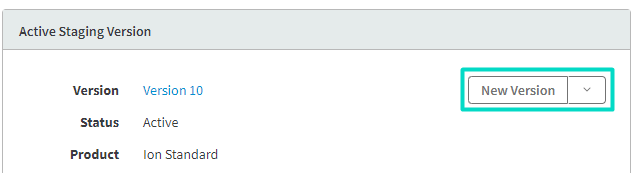
- Create a new version of this property to be able to update it.
You need to create a new version of your property, otherwise you will not be allowed to edit a Property version that is already deployed to Staging and/or Production.
Step 1: Add the following variables and their respective value in the Property Variables section
Please note that Akamai prepends the variables with
PMUSER\_- no need to re-add it.
Required variables
| Variable name | Description | Security settings | Notes |
|---|---|---|---|
| EW_DD_LICENSE_KEY | DataDome server-side key | Hidden | Value of your Server Side Key available in DataDome Dashboard > Management > Integrations |
| EW_DD_DOMAIN | DataDome API endpoint | Hidden | Value: api-akamai.datadome.co |
| EW_CLIENT_IP | Used to get the client IP | Hidden | |
| EW_TLS_VERSION | Used to retrieve the TLS version | Hidden | |
| EW_TLS_CIPHER_NAME | Used to retrieve the TLS Cipher name | Hidden |
Optional variables
Variable name | Description | Security settings | Notes |
|---|---|---|---|
EW_DD_TIMEOUT | DataDome timeout | Hidden | Default value : |
EW_DD_ENABLE_LOGGING | Used to enable logs inside X-DataDome-log response header | Hidden | Value should be |
Step 2: Enable the EdgeWorker
- Scroll down to the Property Configuration Settings panel and click on +Rules and Standard property behavior.
- The Add Rule modal will be shown. Search for Blank Rule Template. For this documentation we will be naming the rule
EW_DD_Rule. Click on the Insert Rule button.
- By default, Akamai adds new rules at the very end of the configuration settings. Scroll to the very bottom of the list and click on the newly added rule. Both the Criteria and Behaviors panels should be empty.
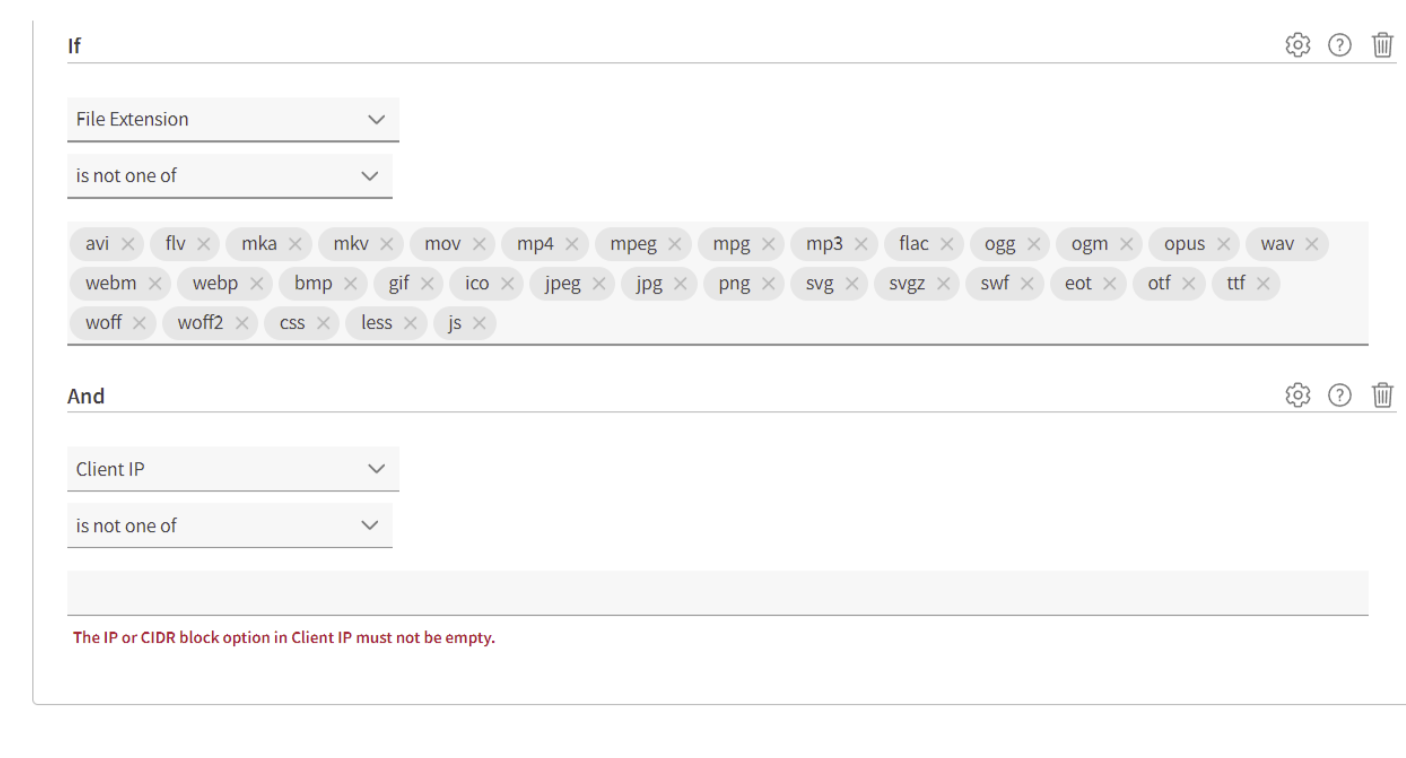
- Add the following criteria in the Criteria panel - this will not forward static file requests to the EdgeWorker
- Criteria:
Match All - Case Sensitive:
Off - Condition _: If
File extension
is not one of
- Criteria:
avi
flv
mka
mkv
mov
mp4
mpeg
mpg
mp3
flac
ogg
ogm
opus
wav
webm
webp
bmp
gif
ico
jpeg
jpg
png
svg
svgz
swf
eot
otf
ttf
woff
woff2
css
less
js
map
txt
json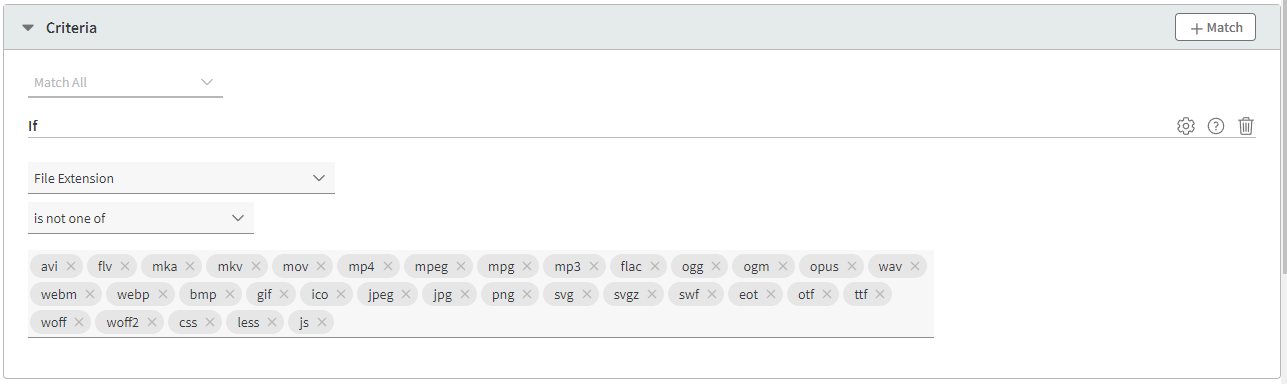
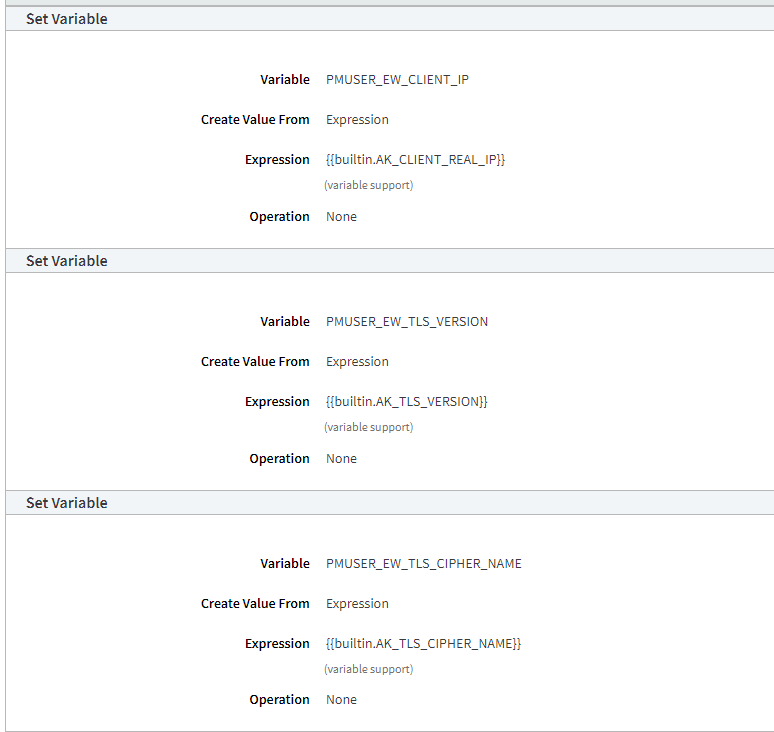
- Add the following behaviors in the Behaviors panel:
Please note that the behaviors need to be added in the order specified in the table
Order | Type | Settings |
|---|---|---|
1 | Set Variable |
|
2 | Set Variable |
|
3 | Set Variable |
|
4 | EdgeWorkers |
|
- Click on the Save button at the top-right or bottom-right.
Step 3: Forward the call from the EdgeWorker to the DataDome API
This part of the installation is required because Akamai EdgeWorkers are not allowed to make subrequests to origins that are not on the Akamai network. For this reason the
/validate-requestpath is mapped to forward the requests to the DataDome API: see Akamai documentation
- Scroll down to the Property Configuration Settings panel and click on +Rules and Standard property behavior.
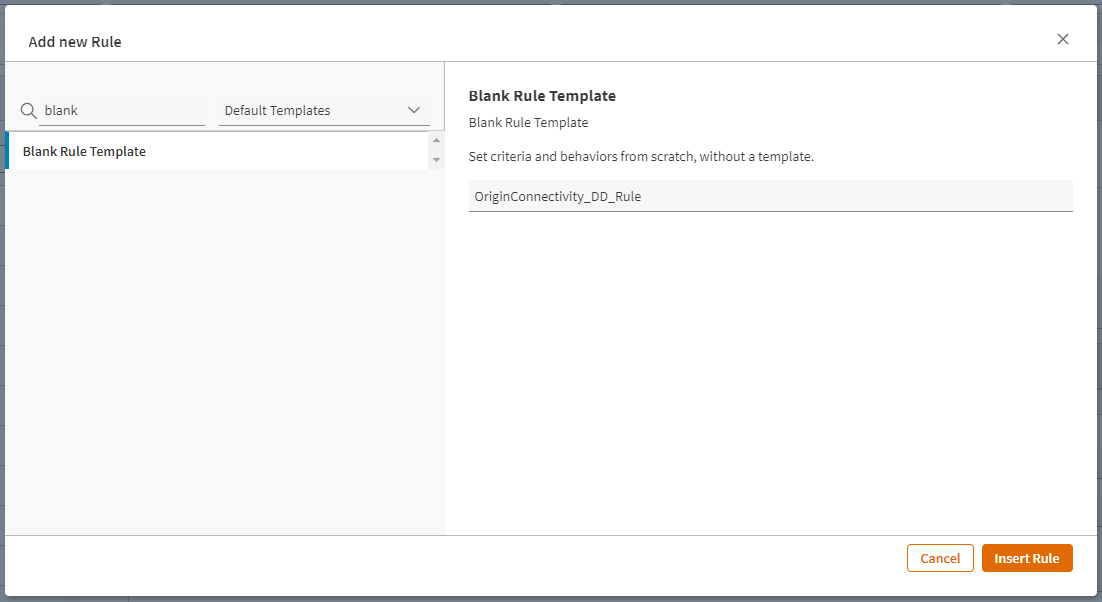
- The Add Rule modal will be shown; search for Blank Rule Template. For this documentation, we will be naming the rule
OriginConnectivity_DD_Rule. Click on the Insert Rule button when done.
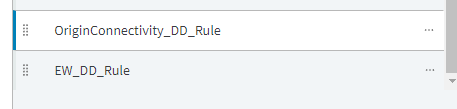
- By default, Akamai adds new rules at the very end of the configuration settings, scroll to the very bottom of the list, and drag this new rule before the previously created
EW_DD_Ruleas in the below screenshot.
-
Click on the newly added rule. Both the Criteria and Behaviors panels should be empty.
-
Add the following Criteria:
- Criteria:
Match All - Condition _: If
Path
matches one of
/validate-request
- Criteria:
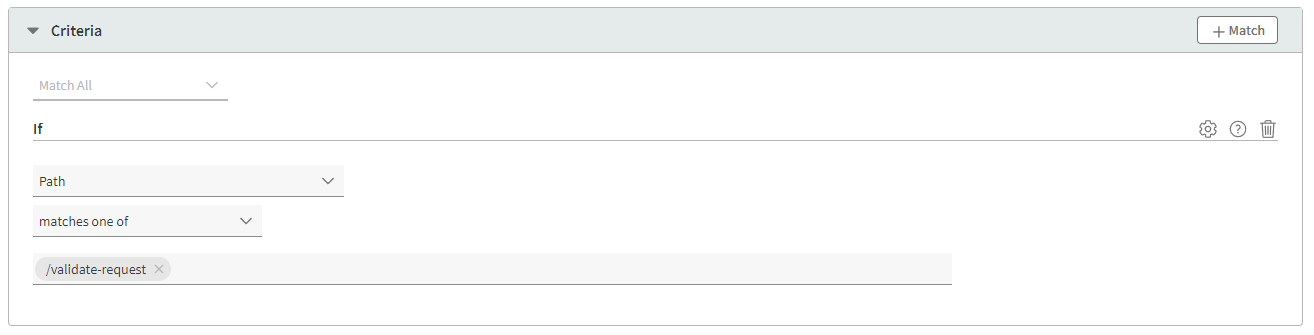
- Click on the +Behavior button (top-right of the Behaviors panel) and add the following:
Type | Settings |
|---|---|
Origin Server | -Origin Type: Your Origin
|
- If you are using Akamai SureRoute, disable it for this rule.
- Click on the Save button at the top-right or bottom-right
Step 4: Bypass mPulse
Please note that this step only applies if the mPulse module is configured in your property
Due to the size of mPulse Javascript and Akamai's limitation on EdgeWorker, when DataDome responds with a challenge, we need to disable mPulse. We only disable it for the CAPTCHA and block page.
- Under the Property Configuration Settings Section, find the Augment Insights >
mPulse RUM rule.
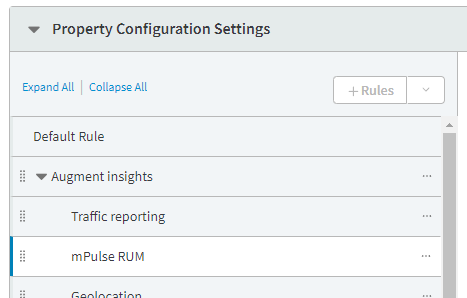
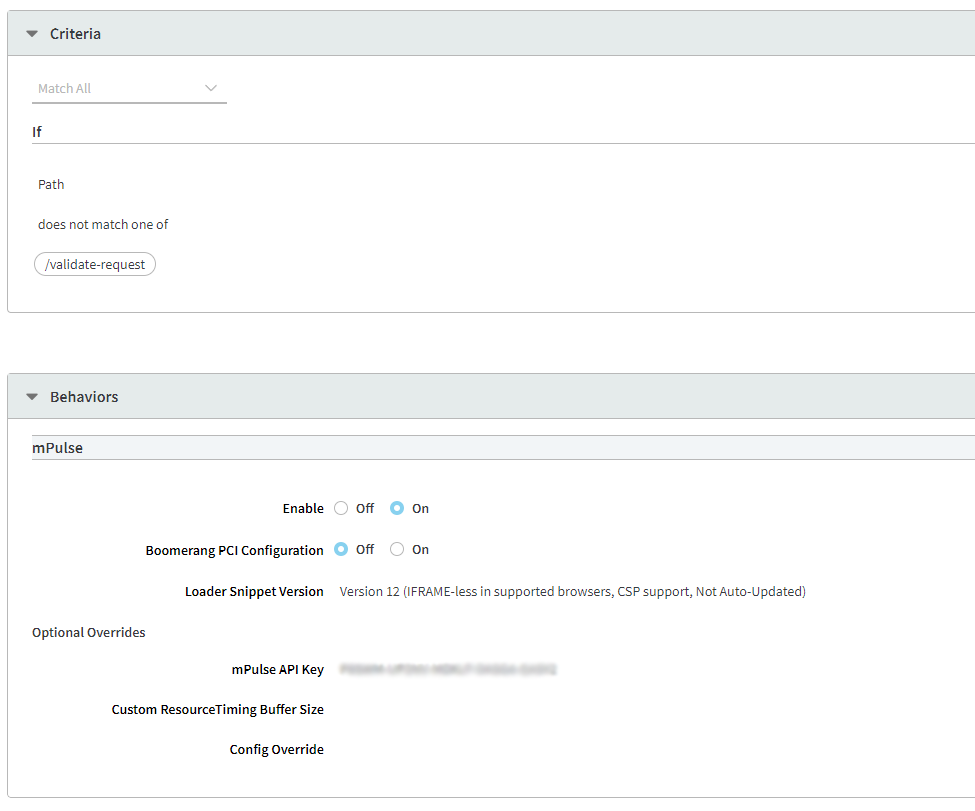
- In the Criteria section, add the following rule:
- Criteria:
Match All - Condition: If
Path
does not matches one of
/validate-request
- Criteria:
Please make sure that the mPulse API key is filled in; this is because the condition set up above will only take effect if this value is provided.
This value can be found by following the steps found at: https://techdocs.akamai.com/mpulse/docs/about-edge-injection.
Step 5: Activate the changes
- Activation is required to test the setup. Switch to the Activate tab at the top.
- Click on the Activate vX on the Staging button, and the Activate version modal will be shown.
It is recommended that deployments are first done in Staging to be validated, then deployed to Production when all the necessary checks are made.
An email address must be provided to receive a notification upon completion of the activation process.
- Click on the Activate vX on Staging button to proceed; the Property version activation details page will get updated with a notification on the top-right and a progress bar.
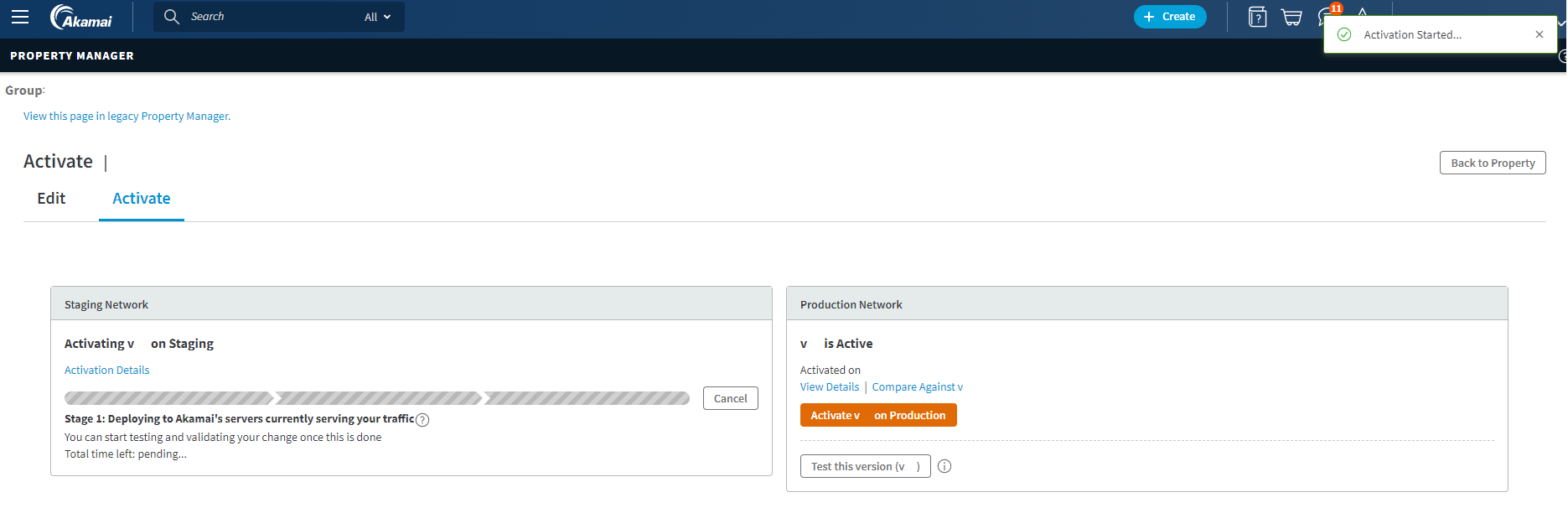
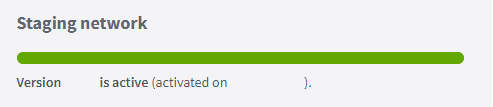
- Kindly wait until the progress bar is full and green, and the version is marked as active in that environment.
Troubleshooting
If you are not seeing any traffic on the DataDome Dashboard, or if challenges are not displayed, follow these steps:
Step 1: Validate Akamai EdgeWorker is executed
- Validate the DataDome variables have been correctly defined inside the
INITIAL VALUEcolumn and not theDESCRIPTIONcolumn. - Make a request to a page that you want to protect, with an additional
Pragmaheader:
Pragma: akamai-x-get-client-ip, akamai-x-cache-on, akamai-x-cache-remote-on, akamai-x-check-cacheable, akamai-x-get-cache-key, akamai-x-get-extracted-values, akamai-x-get-nonces, akamai-x-get-ssl-client-session-id, akamai-x-get-true-cache-key, akamai-x-serial-no, akamai-x-get-request-id, akamai-x-ew-debug- In the response, look for the
x-akamai-edgeworker-onclientresponse-infoandx-akamai-edgeworker-onclientrequest-infoheaders.- If they are present, make sure that the version of the EdgeWorker that has been executed is the one you deployed. In this example, the version is
v1.2.2< x-akamai-edgeworker-onclientresponse-info: ew=61928 v1.2.2-3ef1321:EW_DataDome_Protection; status=Success < x-akamai-edgeworker-onclientrequest-info: ew=61928 v1.2.2-3ef1321:EW_DataDome_Protection; status=Success - If they are not present, verify the rule to call the EdgeWorker is correctly set up (Step 3).
- If they are present, make sure that the version of the EdgeWorker that has been executed is the one you deployed. In this example, the version is
Step 2: Validate DataDome API is being called
- Add the variable
EW_DD_ENABLE_LOGGINGwith the valuetrueinside the Akamai DataDome property.
This will add ax-datadome-logheader to all responses going through the Akamai EdgeWorker. - Redeploy your Akamai property.
- Make a request to a page you want to protect.
- Inspect the HTTP response and look for the
x-datadome-logheader. - Depending on the value of
x-datadome-log, follow the next steps.
Datadome Validate response status code
Datadome Validate response status codeIf the DataDome call status is not 200:
- Ensure
EW_DD_LICENSE_KEYand other variables are correctly set:- Incorrect values may cause
400errors.
- Incorrect values may cause
- Check if the
/validate-requestpath is altered by Akamai and remove it from all policies:- This can lead to
404errors. (The request will be sent to the internal redirect URL instead ofEW_DD_DOMAIN)
- This can lead to
No X-DataDomeResponse in DataDome response
No X-DataDomeResponse in DataDome responseIf there is no X-DataDomeResponse header in the DataDome response, it means that headers are being removed from DataDome HTTP responses by one of your Akamai Policies.
Solution: Remove any policy that can alter DataDome headers.
RangeError: Response body length exceeds limit of 2048
RangeError: Response body length exceeds limit of 2048It means the challenge page returned by DataDome is too large.
Akamai forces the body to be less than 2048 characters and the challenge sent by DataDome is under 2048 characters, but additional services may add content to the response body.
It is generally due to Akamai mPulse Monitoring being enabled for your Property. mPulse adds a lot of JavaScript content inside the page to be able to monitor it.
Solution: You need to disable mPulse for calls to the DataDome API
Setting metadata variable would exceed total variable size limit
Setting metadata variable would exceed total variable size limitIt means the variables set by the EdgeWorker have exceeded the limits of your plan.
By default, the total size limit when creating Property Manager user-defined variables is 1024 characters.
This limit includes the name and value of the variable and only applies to EdgeWorkers added or modified using the JavaScript API.
This error is raised when you are trying to use too many variables in your EdgeWorker.
Solution: Upgrade your EdgeWorker Dynamic Compute tier and contact your Akamai representative to apply this change to your account.
FAQ
How can I exclude IPs and not send traffic to DataDome?
- Akamai allows ClientIP match based on an IP address, a range of IP addresses, or a CIDR block.
- The IP values can be added separated by space, comma, or carriage return.
- For more information, please check Akamai's official documentation page.
How can I use enriched headers in my Akamai property?
Since version 2.0.0 of the module, it is possible to use the value of enriched headers in your Akamai property.
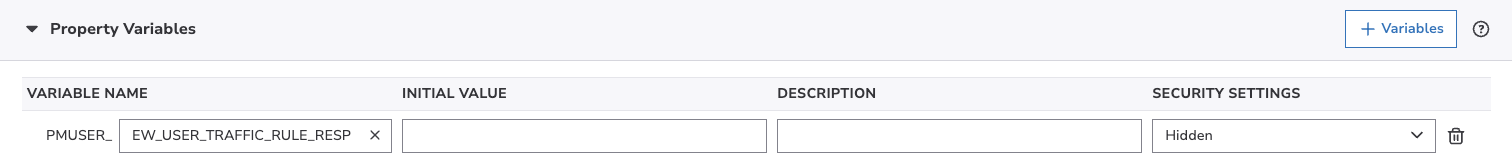
In order to proceed, you need to create a new property variable with the following requirements:
- it must be prefixed with
EW_USER_ - it must contain the enriched header name without the
X-DataDome-prefix - the enriched header name must be in uppercase
- it must not exceed 25 characters due to Akamai's restriction
For example, the X-DataDome-Traffic-Rule-Response header would have its variable named EW_USER_TRAFFIC_RULE_RESP.
Variable limitsThe creation of multiple variables can reach the limits of Akamai variables.
Please refer to this troubleshooting section to fix it.
How can I use Flexible Composition?
Akamai Flexible Composition allows two or more EdgeWorkers to handle a single request. The DataDome module is fully compatible with this architecture.
Before proceeding, make sure the DataDome EdgeWorker is already configured according to our official documentation above. This is a required prerequisite.
We recommend following Akamai’s official documentation to:
Below is an example of the bundle.json and main.js files for a parent EdgeWorker that invokes the DataDome child EdgeWorker:
{
"edgeworker-version": "1",
"description" : "Parent EdgeWorker",
"dependencies": {
"datadome": {
"edgeWorkerId": DATADOME-EDGEWORKER-ID,
"version": "active"
}
}
}If a request is challenged, the DataDome module will generate the response page immediately. Consequently, any subsequent EdgeWorkers in the chain will not be executed.
import * as datadome from "datadome";
export async function onClientRequest(request) {
// Call DataDome child worker for bot protection
await datadome.onClientRequest(request);
// Continue with parent logic if request wasn't challenged
}
export function onClientResponse(request, response) {
// Call DataDome child worker to add response headers
datadome.onClientResponse(request, response);
// Continue with parent logic
}Updated 11 days ago
